NTLM Auditing Just Got a Glow-Up in Windows 11 24H2 & Server 2025
Alright, folks—if you’ve ever found yourself squinting at NTLM logs wondering where this ancient protocol is still lurking in your environment and who is using it, Microsoft just dropped a pretty sweet update that’s going to make your life a whole lot easier.
In case you’re not familiar, NTLM (NT LAN Manager) is like that legacy app you can’t quite get rid of—it’s been around forever, and while it’s not the most secure protocol on the block, it still pops up in enterprise setups thanks to old configurations and stubborn software. Microsoft’s been nudging toward modern authentication (Kerberos), and now they’re giving us better tools to see where NTLM is still being used.
With Windows 11 version 24H2 and Windows Server 2025, NTLM auditing is getting a major upgrade. Think of it as NTLM with a GPS tracker. You’ll now be able to answer:
Who is using NTLM (user account + process name)
Why NTLM was chosen (instead of something modern like Kerberos)
Where it’s happening (machine name + IP address)
And yes, it even flags NTLMv1 usage.
The new NTLM auditing features are configurable through updated Group Policy settings. Administrators can use these policies to specify which NTLM authentication events are audited and to manage auditing behavior across clients, servers, and domain controllers as appropriate for their environment. By default, the events are enabled.
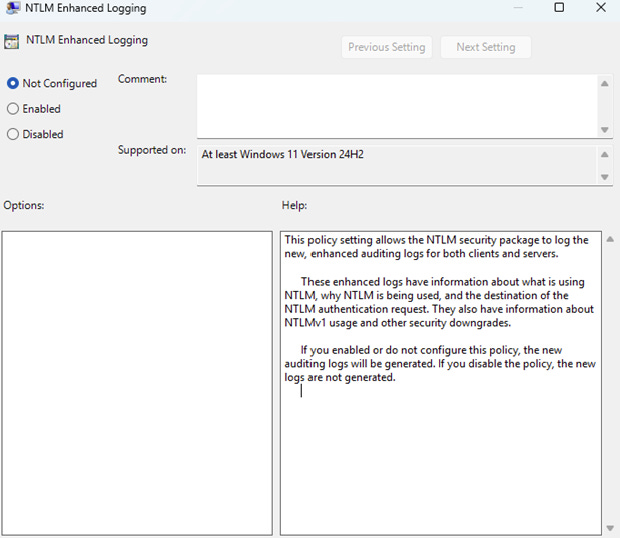
For client and server logging, the events are controlled through the “NTLM Enhanced Logging” policy under Administrative Templates > System > NTLM.
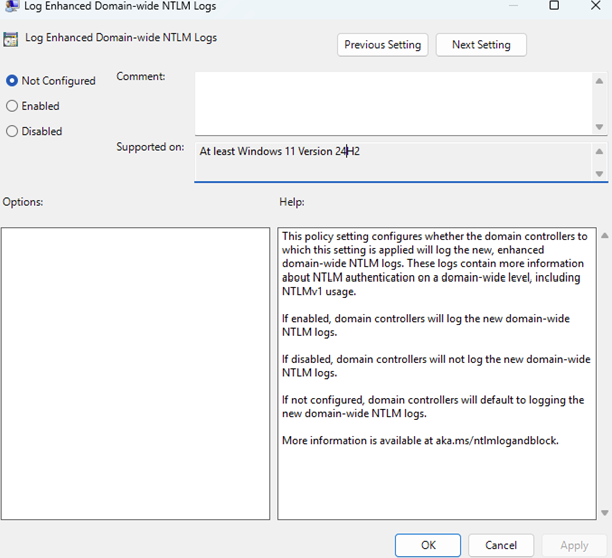
For domain-wide logging on the domain controller, the events are controlled through the “Log Enhanced Domain-wide NTLM Logs” policy under Administrative Templates > System > Netlogon.
All these juicy details show up in Event Viewer under:
Applications and Services Logs > Microsoft > Windows > NTLM > OperationalMicrosoft’s been talking about deprecating NTLM for a while now. These new auditing features help you spot where NTLM is still being used so you can start planning your exit strategy. It’s all part of the broader push toward a more secure, modern authentication landscape.